Like just another day at the office, the cyber-investigator went for a cup of coffee. The 2 investigators sitting on another table discussing a case;
Investigator 1: “Its getting increasingly difficult to track him down, the only update we have is he bought a new (truncated)XXXXXX car for himself. Don’t know where in the whole world he is hiding….”
Investigator 2: “All we can do is try to gather more useful leads….”
What seemed as a dead end lead to investigator’s; for a cyber-investigator the information could be enough to get the case closing.
Enumeration: –
The new vehicle’s are often in it’s default configurations including its Wifi Access point name. Wigle.net allows searching based on Access point names across the regions of interest.

Either of the 3 coordinates definitely could belong to a person of interest. Narrowing down upon a location could further be easy correlating with his other known details.
KEYFOB: –
A remote keyless entry system facilitates the vehicle to be unlocked or started remotely using a mobile device. Software-defined radios are being weaponized by hackers to capture the code used by the car owner to unlock the vehicle. Hackers could then be able to open the car by replaying the process.
Every time the keyfob is used, a different code is sent to the car, which in turn is used to unlock it. Ideally, this would prevent the code from being captured and reused in the future. A flaw however allows reverting the code to an older version, and then open the car by reusing the older code. Further, there is no way to tell if somebody attempts to exploit the flaw in the car as it leaves no traces.
Flaw Profile:
- CVE ID: CVE-2021-4xxx5
- Description: The keyfob subsystem in vehicles allows a replay attack for unlocking. This is related to a non-expiring rolling code and counter-resynchronization.
- Base Score: 5.3
- Severity: MEDIUM
An ability to unlock vehicles could open doors for its further enumeration.


The VIN is a useful piece of information. Connected vehicle platforms available on the market, has a critical bug that affects all major vehicle brands. There are a number of car manufacturers who use telematics and infotainment systems as a part of their vehicle technology.
Vulnerability Analysis
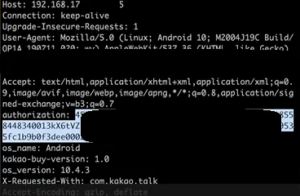
Domain (truncated)http://txxxxxxxxs.net is used during the vehicle enrollment process for remote management. A flaw with the enrollment process for remote management functionality allows tampering with the vehicle. Authorization for exchanging data through the telematics platform needs just the vehicle identification number (VIN) alone. The VIN of the vehicle can therefore be used to carry out a variety of commands by anyone who knows the number. The hacker could log in to the application later on, and then examine the HTTPS traffic that came from a car owner to obtain a bearer token return and a “200 OK” response by passing a VIN prefixed ID through as a customerID as below

Using the Authorization bearer in an HTTP request, information about the user profile of the owner can be obtained leading into successful retrieval of the following information:-
- Name
- Phone number
- Address
- Car details

The extracted information thus leaks the vehicle owners PII.
Wifi Access Point: –






Once the hacker is connected to the vehicle’s AP with the cracked PSK, he can check for all that can be done with the newly obtained access privileges.
Car Hijack
If the vulnerable alarm management account is taken over, many functionalities can be leveraged by hacker from the car alarm app to perform the actions like,
- Geo-locating in real time
- Identification of Car type and owner’s details
- Disabling the alarm
- Unlocking the car
- Enable/disable the immobilizer
- Attempting to ‘Kill’ the car engine during driving
- If privilege allows ‘Snooping’ upon drivers through microphone
- Facilitating in stealing of vehicles
While majority of automobile manufacturers continue to address vulnerabilities that could lead into access to vehicles to perform remote activities like locking/unlocking/starting the car, horn press, headlight flash, locating the car etc… the investigators got a time off to spend with their kids.
Views: 56