Defusing Malwares

Caution/Warning: Hacking back malwares infrastructures (excluding ransomware decryption & recovery) may negatively impact it’s ongoing legal investigations & hence can be…
Sniffing GSM network using SDR scanning
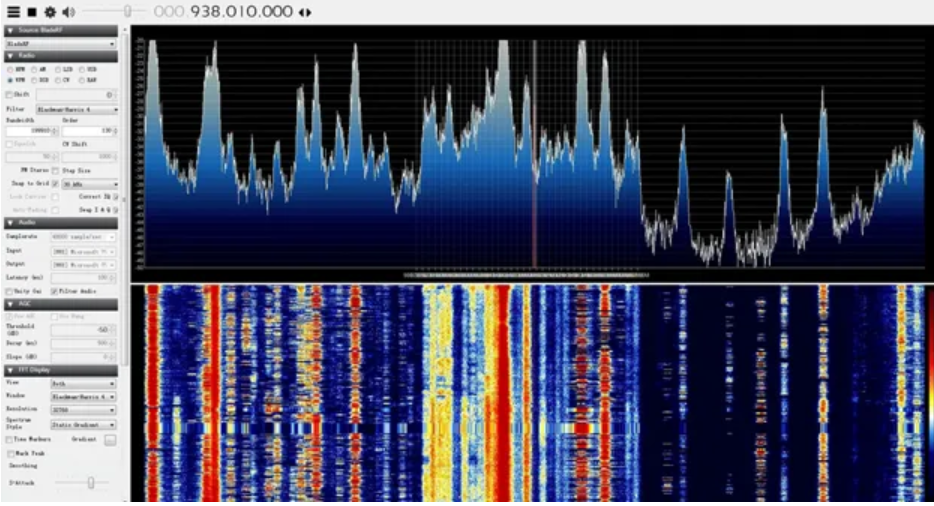
Caution: The research experiments are conducted in faraday bag controlled environment. Any uncontrolled imitation in the real world environment may have regulatory/legal consequences for which you yourself would be responsible! Views: 0
WebAppSec
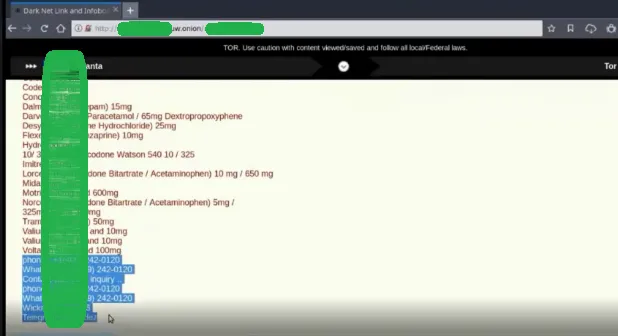
Tor is an anonymous network similar to internet. Websites hosted & activities done upon this network are hence difficult to be traced back to actual users. It thus acts as a breeding ground for various crime networks. Views: 0
Hostage Rescue – Control Systems Security
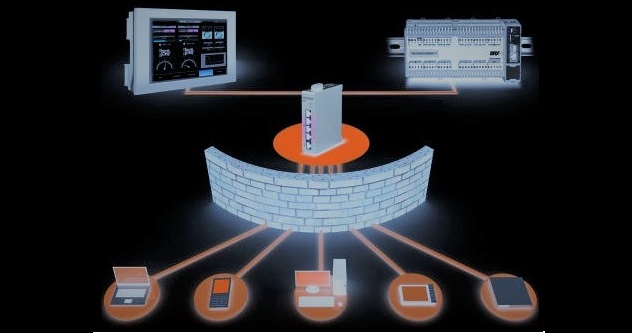
Zero visibility into the indoors resisted soldiers from entering into the hotel with held up hostages. Enumeration: – Environment Automation Servers are used in commercial buildings to control and automate several systems including heating/cooling, ventilation, lighting, security, etc. They can be enumerated as below. Connecting to the Building Automation Server: – The credentials (mostly set […]
Downloaded Kali Linux! What Next?
Numerous intentionally vulnerable systems and applications are widely utilized for educational purposes in the field of cybersecurity. These platforms are specifically created to offer a secure environment for individuals to enhance their abilities in ethical hacking, penetration testing, and vulnerability assessment. Among the notable intentionally vulnerable web applications are Metasploitable, Damn Vulnerable Web Application (DVWA), […]
What is Cyber Range? - A simple Cricket Analogy Perspective.

Disclaimer: This article is purposefully kept long so as to cover most important aspects of Cyber Ranges. Cricket analogy is only for those who are trying to understand the Cyber Range concepts for the first time, others can ignore. What is Cyber Range? Let me start with an analogy . Suppose you want to learn […]
To Track Down a Kingpin – Automotive Security

Like just another day at the office, the cyber-investigator went for a cup of coffee. The 2 investigators sitting on another table discussing a case; Investigator 1: “Its getting increasingly difficult to track him down, the only update we have is he bought a new (truncated)XXXXXX car for himself. Don’t know where in the whole […]
