Defusing Malwares

Caution/Warning: Hacking back malwares infrastructures (excluding ransomware decryption & recovery) may negatively impact it’s ongoing legal investigations & hence can be…
Hostage Rescue – Control Systems Security
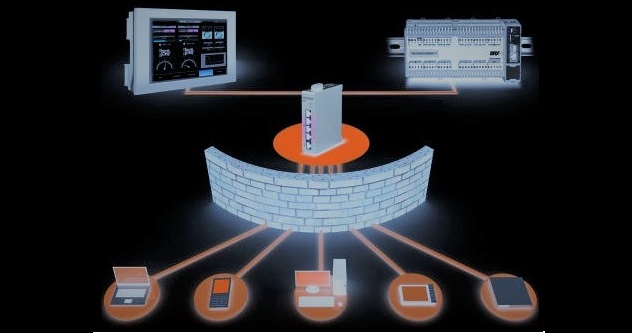
Zero visibility into the indoors resisted soldiers from entering into the hotel with held up hostages. Enumeration: – Environment Automation Servers are used in commercial buildings to control and automate several systems including heating/cooling, ventilation, lighting, security, etc. They can be enumerated as below. Connecting to the Building Automation Server: – The credentials (mostly set […]
Network Latency Troubleshooting
Overview 1. The time a packet takes to travel from Point A to Point B can be referred to as Latency. 2. Latency is expressed in milliseconds 3. The contribu tors to network latency include: 4. Usually, the latency being calculated using network tools such as ping tests & traceroute utility. 5. The ping command measures how long it takes […]
