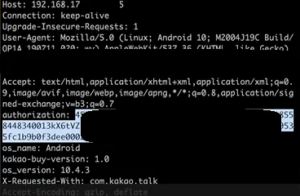
As cyber threats become more sophisticated, the need for skilled cybersecurity professionals continues to grow. Ethical hacking, also known as penetration testing, plays a crucial role in cybersecurity training by equipping professionals with the skills needed to identify and mitigate vulnerabilities before malicious hackers can exploit them. This article explores the importance of ethical hacking in cybersecurity training and how it helps organizations stay ahead of potential threats.
Inspired Tech – Because the future is created by inspiration
What is Ethical Hacking?
Ethical hacking involves authorized attempts to breach an organization’s systems and networks to identify vulnerabilities that could be exploited by malicious hackers. Ethical hackers, also known as “white hat” hackers, use the same techniques as their malicious counterparts but with the goal of improving security rather than causing harm.
Key Components of Ethical Hacking
- Reconnaissance
- Ethical hackers gather information about the target system to understand its architecture and identify potential entry points.
- This phase involves passive techniques (e.g., social media analysis) and active techniques (e.g., network scanning).
- Scanning
- In this phase, ethical hackers use tools to scan the target system for open ports, services, and vulnerabilities.
- Techniques include network scanning, vulnerability scanning, and enumeration.
- Gaining Access
- Ethical hackers attempt to exploit identified vulnerabilities to gain access to the target system.
- This phase tests the effectiveness of an organization’s security measures.
- Maintaining Access
- After gaining access, ethical hackers determine if they can maintain their presence on the system without detection.
- This phase assesses the organization’s ability to detect and respond to intrusions.
- Covering Tracks
- Ethical hackers test their ability to erase evidence of their activities to evaluate the organization’s forensic capabilities.
- This phase highlights the importance of robust logging and monitoring systems.
The Importance of Ethical Hacking in Cybersecurity Training
- Hands-On Experience
- Ethical hacking provides trainees with practical, hands-on experience in identifying and exploiting vulnerabilities.
- This real-world practice is essential for developing the technical skills required to defend against cyber attacks.
- Understanding the Attacker’s Perspective
- By thinking like attackers, trainees can better anticipate potential threats and design more effective security measures.
- Understanding the tactics, techniques, and procedures (TTPs) used by malicious hackers is crucial for developing a proactive defense strategy.
- Enhanced Problem-Solving Skills
- Ethical hacking challenges trainees to think critically and creatively to find solutions to complex security problems.
- This fosters the development of strong analytical and problem-solving skills that are essential in cybersecurity.
- Identifying Security Gaps
- Ethical hacking exercises help organizations identify and address security gaps before they can be exploited by malicious actors.
- Regular penetration testing ensures that security measures remain effective against evolving threats.
- Compliance and Standards
- Many industry standards and regulations require regular penetration testing to ensure compliance.
- Ethical hacking training helps organizations meet these requirements and maintain their security posture.
- Building a Security Culture
- Incorporating ethical hacking into training programs promotes a culture of security awareness and continuous improvement.
- Employees across all levels of the organization become more vigilant and proactive in addressing security risks.
Ethical Hacking Tools and Techniques
- Tools
- Common tools used in ethical hacking include Nmap (network scanning), Metasploit (exploitation framework), and Wireshark (network analysis).
- These tools help ethical hackers identify vulnerabilities, analyze network traffic, and simulate attacks.
- Techniques
- Ethical hackers use a variety of techniques such as social engineering, phishing, and brute force attacks to test an organization’s defenses.
- Advanced techniques may involve exploiting zero-day vulnerabilities or bypassing multi-factor authentication.
The Future of Ethical Hacking in Cybersecurity Training
- Advanced Simulations
- Future ethical hacking training will incorporate more advanced simulations and realistic attack scenarios.
- Virtual environments and cyber ranges will provide immersive training experiences that closely mimic real-world conditions.
- Integration with AI and ML
- AI and machine learning will play a significant role in ethical hacking by automating vulnerability assessments and threat detection.
- Ethical hackers will need to stay updated on these technologies to effectively counter AI-driven cyber threats.
- Interdisciplinary Approaches
- Ethical hacking training will increasingly integrate knowledge from other fields such as psychology, law, and business.
- Understanding the human and organizational aspects of cybersecurity will enhance the effectiveness of ethical hacking efforts.
- Continuous Learning and Certification
- The dynamic nature of cybersecurity requires continuous learning and upskilling.
- Ethical hacking certifications such as Certified Ethical Hacker (CEH) and Offensive Security Certified Professional (OSCP) will remain valuable credentials in the job market.
Conclusion
Ethical hacking is a vital component of cybersecurity training, providing professionals with the skills and knowledge needed to protect organizations from cyber threats. By offering hands-on experience, enhancing problem-solving abilities, and promoting a proactive security culture, ethical hacking ensures that cybersecurity teams are well-prepared to defend against evolving threats. At PurpleSynapz, we are committed to integrating ethical hacking into our training programs, helping organizations build robust defenses and secure their digital assets.
Views: 37