Emerging Trends in Cybersecurity: What You Need to Know

Introduction In today’s digital age, cybersecurity is more critical than ever. As technology advances, so do the tactics of cybercriminals. Staying updated on the latest trends in cybersecurity is essential for protecting your data and systems. This blog will explore the most current and significant trends in cybersecurity that you need to be aware of. […]
How to Start a Career in Cybersecurity: A Step-by-Step Guide

Embarking on a career in cybersecurity can be both exciting and rewarding. With the increasing prevalence of cyber threats, the demand for skilled professionals in this field is at an all-time high. Here’s a step-by-step guide to help you start your journey in cybersecurity. Step 1: Understand the Cybersecurity Landscape Before diving into the field, […]
Top Cybersecurity Job Roles and How to Get Them

The demand for cybersecurity professionals is growing rapidly as organizations seek to protect their digital assets from an increasing array of threats. Here’s a look at some of the top cybersecurity job roles and a guide on how to secure these positions. 1. Security Analyst Role: Security analysts monitor and protect an organization’s computer networks […]
IoT Firmware Exploit Derivation
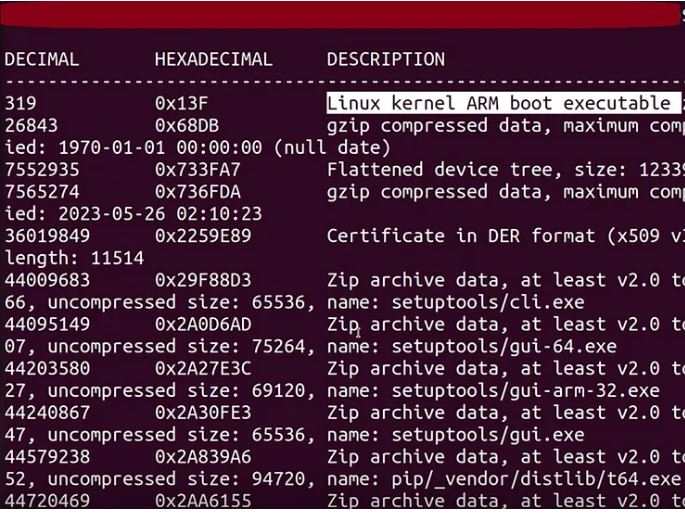
Data shows that only 5% of the CVE’s have publicly available exploits.For the rest of them, we’re just left with CVE’s describing very brief information about the vulnerability & it’s nature. Hits: 0
The Role of Ethical Hacking in Cybersecurity Training

As cyber threats become more sophisticated, the need for skilled cybersecurity professionals continues to grow. Ethical hacking, also known as penetration testing, plays a crucial role in cybersecurity training by equipping professionals with the skills needed to identify and mitigate vulnerabilities before malicious hackers can exploit them. This article explores the importance of ethical hacking […]
Future Trends in Cyber Ranges: What’s Next for Cybersecurity Training?

As the cybersecurity landscape continues to evolve, so too do the methods and tools used to train professionals in the field. Cyber ranges, which are simulated environments designed for cybersecurity training and testing, are at the forefront of this evolution. Here, we explore some of the emerging trends in cyber ranges that are poised to […]
The Rise of AI in Cybersecurity: Benefits and Risks

Introduction Artificial Intelligence (AI) is revolutionizing various industries, and cybersecurity is no exception. As cyber threats become more sophisticated, AI offers promising solutions to enhance defense mechanisms. However, the integration of AI in cybersecurity also brings new challenges and risks. In this article, we explore the benefits and risks associated with the rise of AI […]
Phony Phones — Case Study 9
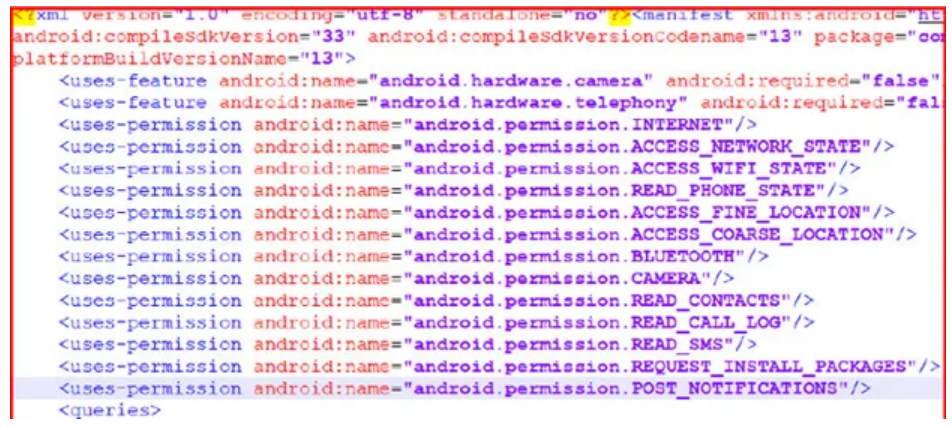
Collecting information about the device’s country and mobile carrier, this malware family often masqueraded as camera apps or other system utilities. It then sent this data to a command-and-control server and received the phone number and SMS message text to send. This technique allowed the malware to operate in different countries and expand into new […]
Phony Phones — Case Study 7&8

Collecting information about the device’s country and mobile carrier, this malware family often masqueraded as camera apps or other system utilities. It then sent this data to a command-and-control server and received the phone number and SMS message text to send. This technique allowed the malware to operate in different countries and expand into new […]
Phony Phones — Case Study 5&6

Collecting information about the device’s country and mobile carrier, this malware family often masqueraded as camera apps or other system utilities. It then sent this data to a command-and-control server and received the phone number and SMS message text to send. This technique allowed the malware to operate in different countries and expand into new […]
