Phony Phones — Case Study 7&8
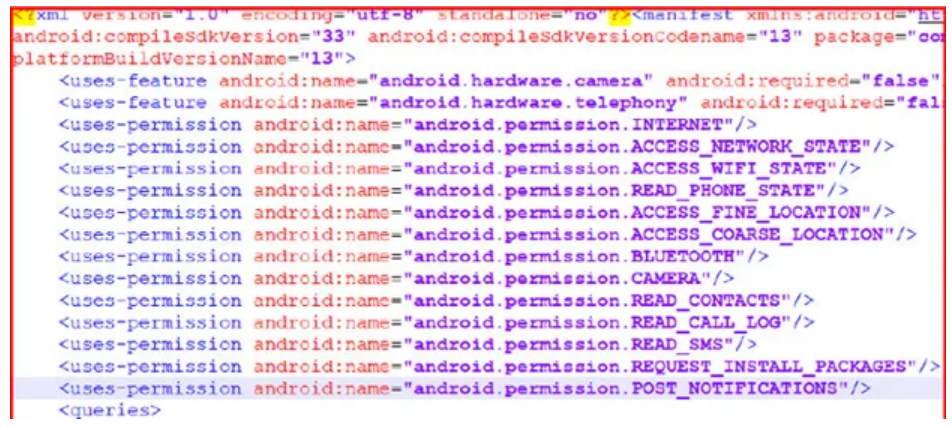
Collecting information about the device’s country and mobile carrier, this malware family often masqueraded as camera apps or other system utilities. It then sent this data to a command-and-control server and received the phone number and SMS message text to send. This technique allowed the malware to operate in different countries and expand into new […]
Phony Phones — Case Study 5&6

Collecting information about the device’s country and mobile carrier, this malware family often masqueraded as camera apps or other system utilities. It then sent this data to a command-and-control server and received the phone number and SMS message text to send. This technique allowed the malware to operate in different countries and expand into new […]
Inside the Mind of a Hacker: Understanding Cyber Threats

Discover the motives and methods of cybercriminals and learn how to defend against them. Read our latest blog post from Purplesynapz to stay one step ahead of cyber threats.
Phishing Scams: How to Recognize and Avoid Them

Introduction Phishing scams are one of the most prevalent forms of cybercrime, targeting individuals and businesses alike. These deceptive attempts to obtain sensitive information can lead to significant financial losses, identity theft, and data breaches. At Purplesynapz, we prioritize educating our community about cybersecurity. In this article, we will explore what phishing scams are, how […]
From Zero to Cyber Hero: Transforming Careers with Intensive Cybersecurity Training

In an era where digital threats are omnipresent, the demand for skilled cybersecurity professionals has never been higher. However, the path to becoming a cybersecurity expert can seem daunting, especially for those starting from scratch. In our latest blog post, “From Zero to Cyber Hero: Transforming Careers with Intensive Cybersecurity Training,” we delve into the […]
Hacking the Hacker: A Hands-On Approach to Cyber Defense Training

In today’s digital landscape, the threat of cyber attacks looms larger than ever. To combat these threats effectively, cybersecurity professionals must adopt a proactive and hands-on approach to training. In our latest blog post, “Hacking the Hacker: A Hands-On Approach to Cyber Defense Training,” we delve into the world of immersive cybersecurity training programs. With […]
Securing Remote Work: Best Practices for Cyber Pro Employees and Employers

Empower Cyber Pros: Secure Remote Work with Purplesynapz
Mastering Cybersecurity: Unveiling 8 Essential Modules of Cyber Pro Training

Introduction: Embarking on the cybersecurity journey requires more than determination; it demands a comprehensive understanding of the digital landscape and the tools and techniques to navigate its complexities. At Purplesynapz, we’re committed to equipping aspiring cybersecurity professionals with the expertise needed to succeed in this dynamic field. Join us as we reveal the 8 essential […]
Phony Phones — Case Study 3&4

Collecting information about the device’s country and mobile carrier, this malware family often masqueraded as camera apps or other system utilities. It then sent this data to a command-and-control server and received the phone number and SMS message text to send. This technique allowed the malware to operate in different countries and expand into new […]
Phony Phones — Case Study 1&2

Collecting information about the device’s country and mobile carrier, this malware family often masqueraded as camera apps or other system utilities. It then sent this data to a command-and-control server and received the phone number and SMS message text to send. This technique allowed the malware to operate in different countries and expand into new […]
